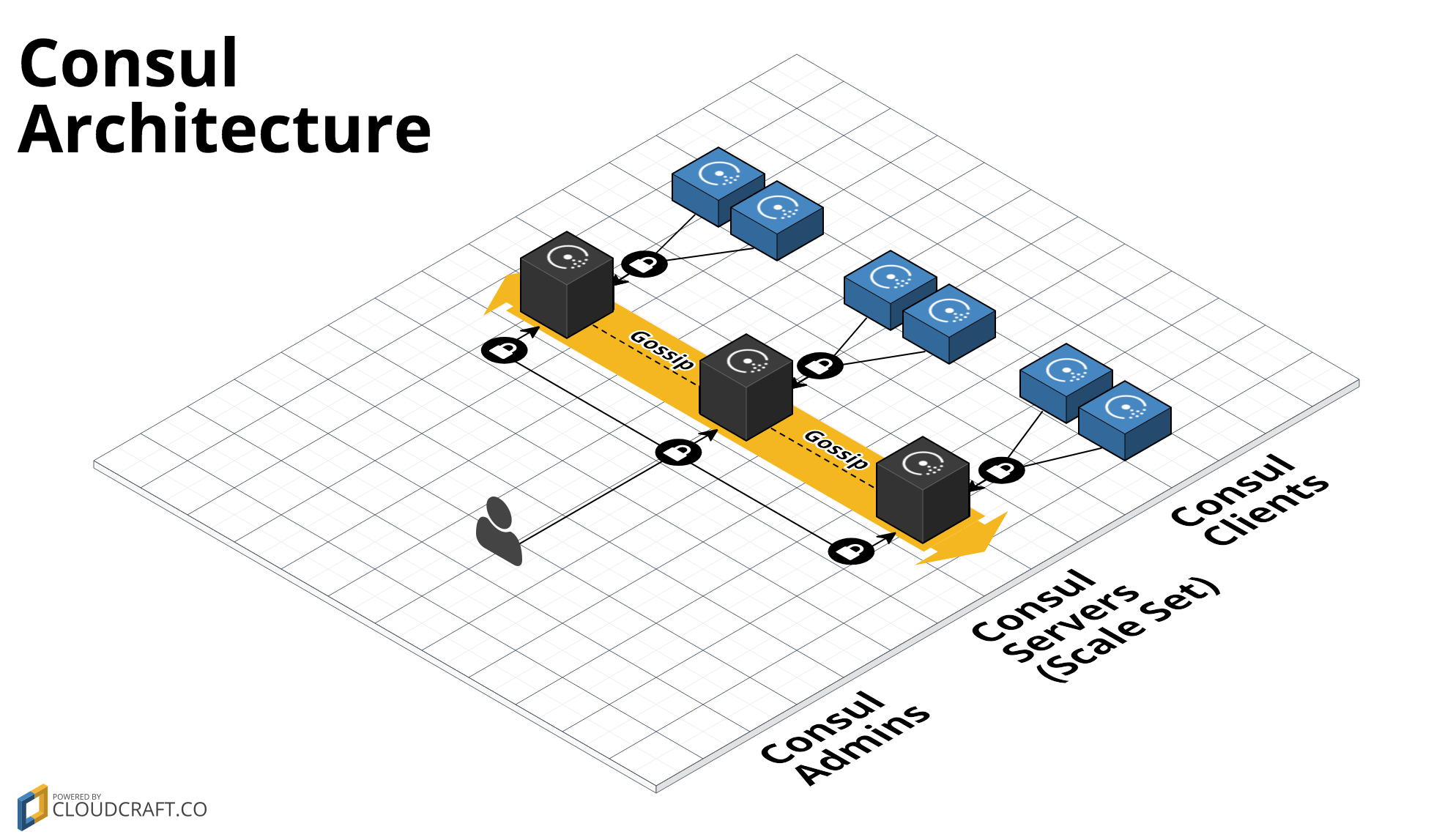
This repo contains a Module for deploying a Consul cluster on Azure using Terraform. Consul is a distributed, highly-available tool that you can use for service discovery and key/value storage. A Consul cluster typically includes a small number of server nodes, which are responsible for being part of the consensus quorum, and a larger number of client nodes, which you typically run alongside your apps:
Each Module has the following folder structure:
- root: This folder shows an example of Terraform code that uses the consul-cluster module to deploy a Consul cluster in Azure
- modules: This folder contains the reusable code for this Module, broken down into one or more modules.
- examples: This folder contains examples of how to use the modules.
To deploy Consul servers using this Module:
-
Create a Consul Image using a Packer template that references the install-consul module. Here is an example Packer template.
-
Deploy that Image in a Scale Set using the Terraform consul-cluster module and execute the run-consul script with the
--serverflag during boot on each Instance in the Scale Set to form the Consul cluster. Here in the root is an example Terraform configuration to provision a Consul cluster.
To deploy Consul clients using this Module:
- Use the install-consul module to install Consul alongside your application code.
- Before booting your app, execute the run-consul script with
--clientflag. - Your app can now using the local Consul agent for service discovery and key/value storage.
- Optionally, you can use the install-dnsmasq module to configure Consul as the DNS for a
specific domain (e.g.
.consul) so that URLs such asfoo.service.consulresolve automatically to the IP address(es) for a servicefooregistered in Consul (all other domain names will be continue to resolve using the default resolver on the OS).
A Module is a canonical, reusable, best-practices definition for how to run a single piece of infrastructure, such as a database or server cluster. Each Module is created using Terraform, and includes automated tests, examples, and documentation. It is maintained both by the open source community and companies that provide commercial support.
Instead of figuring out the details of how to run a piece of infrastructure from scratch, you can reuse existing code that has been proven in production. And instead of maintaining all that infrastructure code yourself, you can leverage the work of the Module community to pick up infrastructure improvements through a version number bump.
This Module is maintained by Gruntwork. If you're looking for help or commercial support, send an email to [email protected]. Gruntwork can help with:
- Setup, customization, and support for this Module.
- Modules for other types of infrastructure, such as VPCs, Docker clusters, databases, and continuous integration.
- Modules that meet compliance requirements, such as HIPAA.
- Consulting & Training on AWS, Terraform, and DevOps.
-
install-consul: This module installs Consul using a Packer template to create a Consul Azure Image.
-
consul-cluster: The module includes Terraform code to deploy a Consul Image in a Virtual Machine Scale Set.
-
run-consul: This module includes the scripts to configure and run Consul. It is used by the above Packer module at build-time to set configurations, and by the Terraform module at runtime with Custom Data to create the cluster.
-
install-dnsmasq module: Install Dnsmasq and configure it to forward requests for a specific domain to Consul. This allows you to use Consul as a DNS server for URLs such as
foo.service.consul. -
consul-security-group-rules: Defines the security group rules used by a Consul cluster to control the traffic that is allowed to go in and out of the cluster.
Contributions are very welcome! Check out the Contribution Guidelines for instructions.
This Module follows the principles of Semantic Versioning. You can find each new release, along with the changelog, in the Releases Page.
During initial development, the major version will be 0 (e.g., 0.x.y), which indicates the code does not yet have a
stable API. Once we hit 1.0.0, we will make every effort to maintain a backwards compatible API and use the MAJOR,
MINOR, and PATCH versions on each release to indicate any incompatibilities.
This code is released under the Apache 2.0 License. Please see LICENSE and NOTICE for more details.